Intro
After tirelessly looking for a solution in order to dynamically create a whitelist for Suricata based on DNS, I decided to create my own.
Download the necessary files
Create a whitelist file with all the domains you wish whitelisted. A useful starting point is anudeepND’s collection of commonly white listed domains. After that, download my generateRules.py script.
Place these files in a directory of your choice on your pfSense host. For simplicity, I just placed them in /root. Finally, make the script executable by chmod +x ./generateRules.py.
Modifying suricata.inc
Navigate to /usr/local/pkg/suricata/ and using a text editor open suricata_defs.inc. Make the following modifications:
if (!defined("SURICATA_DEFAULT_RULES"))
define("SURICATA_DEFAULT_RULES", array( "whitelist.rules","app-layer-events.rules",
"decoder-events.rules", "dhcp-events.rules", "dnp3-events.rules",
"dns-events.rules", "files.rules", "http-events.rules",
"http2-events.rules", "ipsec-events.rules", "kerberos-events.rules",
"modbus-events.rules", "mqtt-events.rules", "nfs-events.rules",
"ntp-events.rules", "smb-events.rules", "smtp-events.rules",
"ssh-events.rules", "stream-events.rules", "tls-events.rules"));The first element in the array will be our generated whitelist.rules. This file can be named as you wish and it will appear as so in the web gui.
Running the script
Run the script with the path to the dns whitelist as well as where you want the output file. For example:
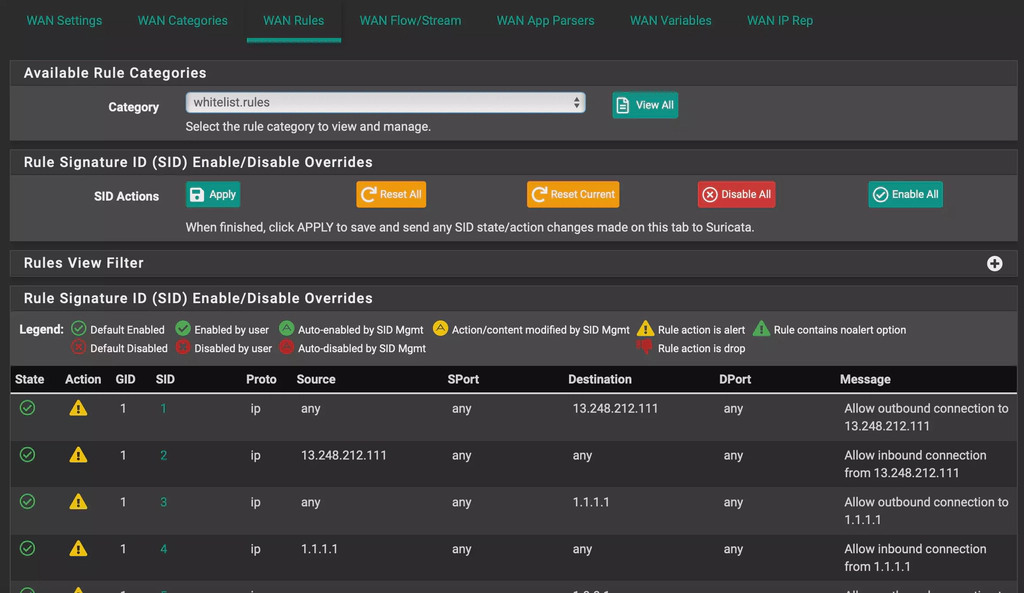
./generateRules.py /root/dns_list.txt /root/whitelist.rulesOnce the script has finished, you can copy/move it to /usr/local/share/suricata/rules/. If you open the Suricata web gui and select your interface, the new ruleset should appear. If not, you can try running suricata-update in terminal.
Automating the generation of rules
Since the IPs can change for any given domain, an easy way to update them would be to set up a cron job. Mine looks like this:
0 0 * * * /root/update_rules.py /root/dns_list.txt /root/whitelist.rules
35 0 * * * mv /root/whitelist.rules /usr/local/share/suricata/rules/whitelist.rules && suricata-updateDone!
After these steps are done, you are good to go and your domains will be whitelisted.