Intro
At the time of writing this post, I found no guide on setting up Authelia as a social provider for ERPNext. These are the steps I took to link them.
Authelia
If you have an LDAP server configured, you have to make sure the correct attributes are retrieved. The attributes section should look like follows.
authentication_backend:
ldap:
implementation: custom
address: ldap://<server ip address>:389
start_tls: false
tls:
skip_verify: true
minimum_version: TLS1.2
base_dn: DC=mydomain,DC=com
attributes:
username: sAMAccountName
group_name: cn
mail: mail
display_name: displayname
given_name: givenName
family_name: sn
users_filter: (&(|({username_attribute}={input})({mail_attribute}={input}))(objectCategory=person)(objectClass=user)(!userAccountControl:1.2.840.113556.1.4.803:=2)(!pwdLastSet=0))
groups_filter: (&(member:1.2.840.113556.1.4.1941:={dn})(objectClass=group)(objectCategory=group))
user: CN=<bind account username>,CN=Users,DC=mydomain,DC=com
password: <bind account password>Once the ldap section is correct, you should proceed to the identity providers section to configure the ERPNext client. The client configuration for erpnext should look as follows:
identity_providers:
oidc:
clients:
- client_id: erpnext
client_name: erpnext
client_secret: '$pbkdf2-sha512$310000$OYxF/9Lo7Rv1K30g3UH0bg$nH9ZVUX9zEYGPHnHHFbueWz6TbpHsdvjx.WgYGGwd31sRV.CIgGXz4EW0fwOuPpI9fiv2G8cyowb/zD8A8LiCg'
public: false
authorization_policy: one_factor
redirect_uris:
- https://<erpnext domain>/api/method/frappe.integrations.oauth2_logins.custom/authelia
scopes:
- openid
- profile
- email
- groups
userinfo_signed_response_alg: none
consent_mode: implicit
token_endpoint_auth_method: 'client_secret_post'To generate the client secret, you will have to issue the command docker run --rm authelia/authelia:latest authelia crypto hash generate pbkdf2 --variant sha512 --random --random.length 72 --random.charset rfc3986
The output should look like follows.
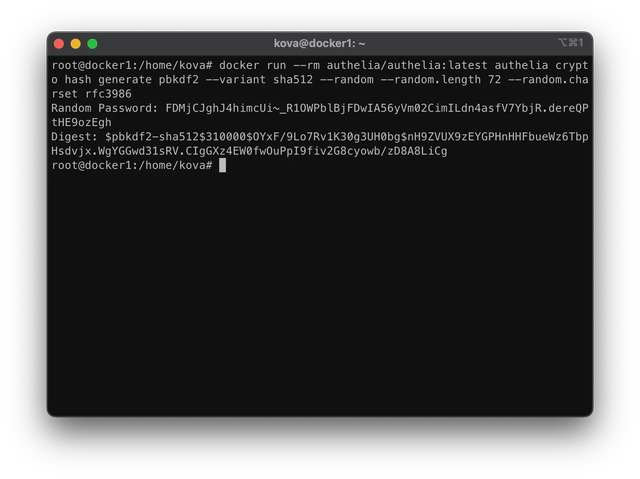
The digest will be used in the Authelia client configuration, as shown above. Copy the random password and keep it handy, as that will be used in the ERPNext configuration. Restart Authelia for the changes to take effect.
ERPNext Configuration
In the dashboard, navigate to Integrations -> Social Login Key -> Add Social Login Key. The form can be filled as follows:
Client Credentials
- Social Login Provider: Custom
- Provider Name: Authelia
- Client ID: erpnext or whatever client id you used in the Authelia configuration
- Client Secret: paste the random password generated in the previous step
Identity Details
- Icon: can leave blank or provide a url for an Authelia icon
- Base URL: https://<authelia domain>
Configuration
- Sign Ups: Allow
Client URLs
- Authorize URL: /api/oidc/authorization
- Redirect URL: https://<erpnext domain>/api/method/frappe.integrations.oauth2_logins.custom/authelia
- Access Token URL: /api/oidc/token
- API Endpoint: /api/oidc/userinfo
Client Information
- API Endpoint Args: empty
- Auth URL Data:
{"scope": "openid profile email", "response_type": "code"} - User ID Property: email
Make sure to click Enable Social Login and click on Save. If you wish to disable regular username login, navigate to System Settings -> Login and check Disable Username/Password Login. Click Save
Done!
If everything is set up correctly, you will be able to login with Authelia.